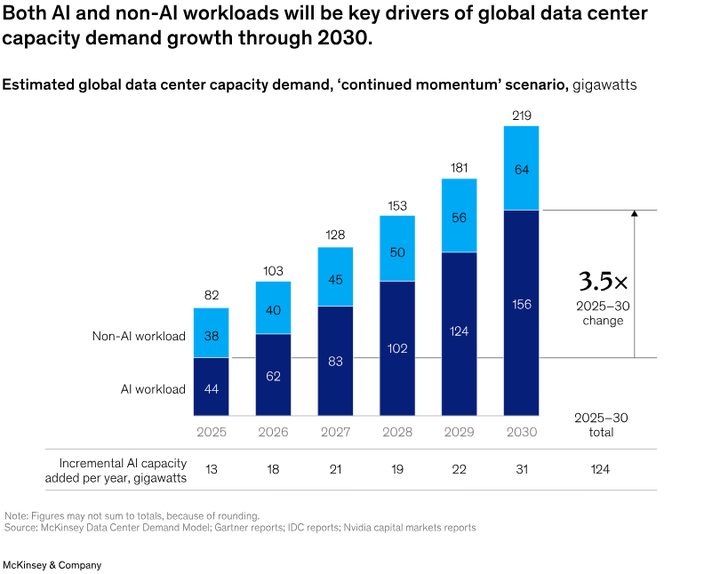
Global compute demand is exploding at a scale never seen before. According to McKinsey, data centers will require nearly $7 trillion in investment by 2030, with AI workloads alone driving $5.2 trillion of that demand as enterprises race to train and deploy increasingly complex models. ZK proofs, AI inference, model training, and high-performance cryptographic workloads consume billions of dollars in GPUs, ASICs, and power each year, but most of this compute remains locked inside centralized, siloed infrastructure where it is expensive, inaccessible, and impossible to monetize.
Estimates of global compute demand | Source: McKinsey & Co
Cysic Network (CYS) addresses this gap by becoming the world’s first full-stack decentralized compute network, combining custom ZK ASICs, GPU clusters, portable miners, and an EVM-compatible
Cosmos blockchain into a programmable, liquid ComputeFi economy. With $12 million in pre-A funding and integrations with Aleo,
zkSync,
Scroll, Axiom, Nil,
Talus, and Herodotus, Cysic is rapidly establishing itself as the foundational infrastructure for
ZK proofs,
AI agents, and verifiable computation at scale.
Discover what Cysic is, how ComputeFi works, what powers the CYS token, and how you can trade CYS on BingX.
What Is Cysic Network (CYS)?
Cysic Network is a full-stack decentralized compute layer built to transform physical hardware, like GPUs, ASICs, servers, and mining rigs, into liquid, yield-bearing, on-chain assets. Unlike networks that only coordinate compute, Cysic builds both the hardware and the blockchain that runs it, enabling high-performance ZK proof generation, AI inference, cryptographic computation, and digital mining.
Cysic’s growth is backed by strong fundamentals and industry adoption. The project has raised $12 million from top investors including Polychain, HashKey, OKX Ventures, ABCDE, Matrixport, and IDG, and is deploying ZK-specific ASICs capable of millions of Keccak computations per second alongside custom GPU servers and portable miners optimized for verifiable compute. Its EVM-compatible Cosmos CDK chain coordinates provers, verifiers, and stakers, while integrations with leading ZK ecosystems, Aleo, zkSync, Scroll, Nil, Axiom, Talus, and others, position Cysic as a core infrastructure layer for the next generation of scalable cryptography and
AI workloads.
Cysic’s goal is simple: turn compute into programmable capital, the “missing pillar” alongside DeFi, storage, and bandwidth.
How Does Cysic Network Work?
Cysic operates as a vertically integrated stack across four layers, each designed to make compute trustless, scalable, and monetizable.
1. Hardware Layer: ZK ASICs, GPU Clusters, Portable Miners
Cysic’s foundation starts with real, high-performance hardware built specifically for ZK proofs and AI workloads. Its ZK ASICs deliver proving speeds far beyond standard GPUs while using less energy, and its GPU servers run optimized CUDA kernels for fast, verifiable AI inference. For everyday users, portable miners and small-scale rigs make it easy to contribute compute power without needing a data center. The network also supports third-party GPUs and HPC clusters, so anyone with compatible hardware can plug in and earn CYS. This entire layer acts like “ComputeFi hashpower,” but unlike
Bitcoin mining, the compute can be used for many workloads, not just securing a blockchain.
2. Cysic's Proof of Compute (PoC) Consensus Layer
Cysic upgrades the standard Cosmos CometBFT engine with Proof of Compute (PoC), a system where validators are chosen not just by how many tokens they stake, but also by how much real compute power they contribute and how reliably they perform tasks. In PoC, nodes that deliver faster, correct ZK proofs or AI inference results earn higher reputation and influence block production.
This approach ensures all computation on the network is verifiable, workloads are distributed fairly across provers, and the chain’s security grows with real hardware participation, not just token ownership. In simple terms, PoC turns Cysic into a compute-backed blockchain, where useful work strengthens the network.
3. Execution Layer: Job Routing, Verification, and Settlement
The execution layer is where real compute tasks get assigned, processed, and paid for. Cysic’s smart contracts automatically route jobs, whether they’re ZK proofs, AI inference tasks, or compute rentals, to the fastest available hardware on the network. Provers generate proofs, verifiers check correctness, and rewards are settled on-chain.
This layer also powers the Digital Compute Marketplace, where compute can be tokenized and traded, and includes essential EVM features like bridging, swapping, and governance. For beginners, think of it as the “matchmaking engine” that connects compute buyers with compute providers, ensuring every task is processed cheaply, quickly, and verifiably.
4. Product Layer: ComputeFi Applications
The product layer turns Cysic’s hardware and blockchain infrastructure into tools that developers and everyday users can actually use. The ZK Proof Market lets projects outsource proof generation with a single interface, while Cysic AI offers cheap, fast compute for running or training AI models. Users can also earn yield through Digital Mining, where compute power becomes a tokenized, income-generating asset.
For builders of ZK rollups, AI apps, or autonomous agents, Cysic acts as a plug-and-play backend, providing verifiable compute without needing to manage expensive hardware or cloud infrastructure.
What Are the Real Use Cases of Cysic Network?
Cysic enables decentralized, verifiable compute across multiple high-demand verticals, making it useful for both developers and hardware contributors. At the protocol level, Cysic’s ZK ASICs, GPU clusters, and prover network power workloads that traditionally require expensive centralized infrastructure, bringing lower costs, higher throughput, and cryptographic assurance to compute-intensive tasks.
1. Zero-Knowledge Proof Generation (ZKPs): Projects building rollups, coprocessors, and privacy systems can outsource proving to Cysic’s decentralized prover network. Purpose-built ZK ASICs accelerate millions of Keccak computations per second, cutting proving time and reducing costs for systems like Aleo, zkSync, Scroll, and Nil.
2. AI Inference and Model Serving: Cysic AI allows developers to run inference workloads, LLMs, vision models, agent workflows, on decentralized GPU clusters at significantly lower cost than centralized cloud providers. Verifiable compute ensures outputs can be trusted in financial, legal, or security-sensitive use cases.
3. Compute-Backed Digital Mining: Users with compatible hardware like ZK ASICs, GPU rigs, or portable miners can contribute compute cycles to the network and earn CYS. This model transforms raw compute into an income-generating asset, similar to mining but for ZK proofs, inference tasks, and high-performance workloads.
4. Agentic Automation and On-Chain Verification: AI agents can execute workflows that rely on verifiable compute, such as automated trading, compliance checks, simulations, or risk scoring, while Cysic guarantees correctness through prover–verifier coordination.
5. Governance and Compute Allocation: CYS holders can stake tokens to participate in governance and influence network decisions such as compute pricing, reward schedules, product rollout, and ecosystem partnerships.
What Is the CYS Token Utility?
CYS is the native token that powers the entire compute economy.
1. Gas and Transaction Fees: CYS is used across the EVM-compatible chain to pay gas, settle proofs, and process compute tasks.
2. Compute Rewards: Provers, validators, miners, and agents earn CYS for contributing compute or verifying workloads.
3. Staking and Security: Staking CYS secures the network and assigns provers/verifiers to high-value tasks.
4. Governance via CGT (veToken Model)
• Stake CYS → receive CGT 1:1
• Long-term lockups boost governance weight
• CGT influences compute allocation and reward distribution
5. Digital Mining Rewards: Owners of Cysic hardware receive rewards proportional to performance and uptime.
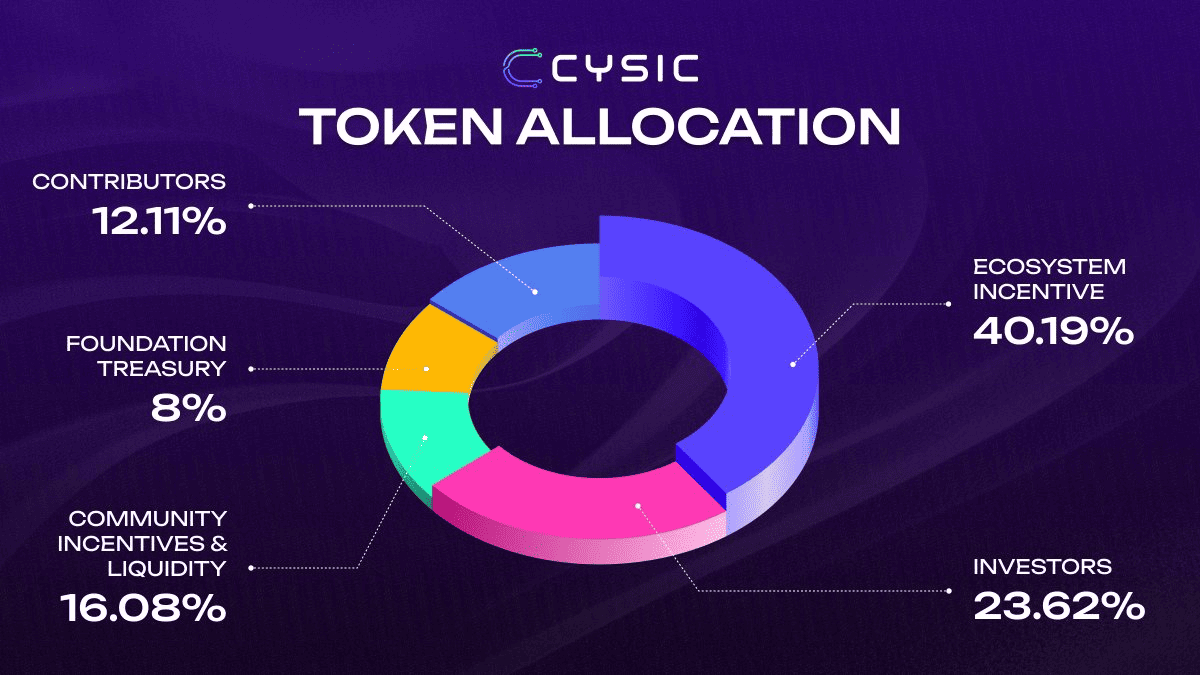
CYS Tokenomics Overview
Cysic launched with a fixed supply of 1 billion CYS, of which 160.8 million tokens entered circulation at TGE. The supply is non-inflationary, with no planned emissions and the potential for future burn mechanisms to make CYS increasingly deflationary over time.
CYS token allocation | Source: Cysic Foundation on X
CYS Token Distribution
• Ecosystem Incentives — 40.19%
• Investors — 23.62%
• Community Incentives & Liquidity — 16.08%
• Contributors — 12.11%
• Foundation Treasury — 8%
Some categories include 50% immediate unlock at TGE and 50% linear vesting over six months, aligning early users with long-term network growth.
How to Claim Cysic (CYS) Airdrop
Source: Cysic
Claiming your CYS tokens is straightforward, but you must use the correct wallet and follow the official portal to avoid losing eligibility. The airdrop unlocks 50% of your tokens at TGE, with the remaining 50% released linearly over six months.
1. Visit the official Cysic Airdrop Portal: Go to the
verified CYS claim page shared by Cysic’s official website or social channels. Avoid third-party links.
2. Connect your Keplr wallet: Use the same Keplr wallet tied to your testnet activity, NFT redemption, or partner program allocations. This ensures your CYS rewards are detected correctly.
3. Check your eligibility: The dashboard will display your CYS allocation, including unlocked and vesting amounts tied to the 50/50 distribution schedule.
4. Approve the claim transaction: Confirm the on-chain transaction in Keplr. You may need a small amount of gas tokens to complete the claim.
5. Receive your CYS tokens: Your unlocked tokens will appear instantly, while the remaining balance will vest automatically over the six-month period.
Once claimed, you can hold, stake, or trade your CYS, including on BingX Spot and Futures, where users can take advantage of BingX AI tools for analysis and execution.
How to Trade Cysic (CYS) on BingX
CYS is listed on BingX Spot and Futures, giving you full exposure to ComputeFi.
Buy or Sell CYS/USDT on Spot Trading
CYS/USDT trading pair on the spot market powered by BingX AI insights
1. Create or log in to your BingX account.
5. Execute the trade and monitor your holdings.
Long or Short CYSUSDT Perpetuals on Futures Trading
CYS/USDT perpetual contract on the futures market powered by BingX AI
1. Launch
BingX Futures and transfer USDT to your Futures Wallet.
3. Set leverage and margin mode.
4. Open long or short positions based on market outlook.
5. Manage
TP/SL (take-profit, stop-loss) and monitor liquidation levels.
BingX AI tools help you trade CYS more intelligently by generating real-time market insights, sentiment summaries, and trend analysis. You can also set
automated DCA plans and price alerts, making it easier to manage positions and react quickly to market movements.
What Makes Cysic Different From Other AI Crypto Projects?
Cysic differentiates itself through full-stack vertical integration, owning both the hardware layer and the blockchain protocol that coordinates and monetizes compute. While most AI or ZK networks rely on third-party GPUs or cloud resources, Cysic deploys its own ZK ASICs, GPU servers, and portable miners, delivering significantly faster proving performance, lower AI inference costs, and more efficient proof settlement. This hardware advantage is reinforced by its EVM-compatible Cosmos CDK chain, which secures provers, verifiers, and stakers under a unified Proof-of-Compute model.
Beyond performance, Cysic offers a modular ComputeFi economy that combines zero-knowledge proofs, AI workloads, high-performance computing, and digital mining into one programmable system. Verifiable compute is guaranteed through on-chain incentives and correctness checks, critical for ZK rollups, AI agents, and autonomous execution environments. Backed by Polychain, HashKey, SNZ, Web3.com, Matrixport, and other major investors, Cysic is rapidly integrating across leading ZK ecosystems, positioning it as a foundational layer for next-generation computation.
Conclusion
Cysic Network represents a major leap forward in how compute is created, priced, and consumed on-chain. By unifying hardware, cryptography, AI, and blockchain into a single ComputeFi marketplace, Cysic offers developers, provers, miners, and users a more efficient and decentralized foundation for the next era of computation.
As with all emerging networks, CYS carries risks, from token volatility to adoption uncertainty. Start small, use reliable exchanges like BingX, and always follow official Cysic channels for updates.
Related Reading